Review of Predator by Richard Goutorbe
Predator is an innovative software application designed for professionals in various fields, primarily focusing on cybersecurity and network management. Developed by Richard Goutorbe, this tool has gained traction among IT specialists due to its comprehensive features aimed at streamlining security protocols and enhancing data protection. This review will explore Predator's key functionalities, benefits, user interface, and overall performance.
Key Features
- Real-time Threat Detection: Predator excels in identifying potential threats in real-time, employing advanced algorithms to monitor system behavior and detect anomalies.
- Automated Response Solutions: One of the standout features includes automated responses to detected threats, which help prevent breaches and mitigate damages proactively.
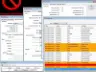
- User-Friendly Dashboard: The application is equipped with an intuitive dashboard that allows users to visualize threats, analyze potential vulnerabilities, and generates detailed reports.
- Integration with Existing Systems: Predator offers seamless integration with a variety of existing systems and software tools, simplifying the adoption process for organizations.
- Customizable Alerts: Users can set up customizable alerts to receive notifications based on specific criteria, thus ensuring a tailored security approach.
User Interface
The user interface (UI) of Predator is designed with usability in mind. Upon launch, users are greeted with a clean layout that emphasizes ease of navigation. The dashboard displays critical information at a glance, allowing professionals to quickly assess the security posture of their networks.
The color-coded notifications simplify understanding the urgency of threats. Users can easily access various functionalities through well-organized menus. This focus on design ensures that even those who may not have extensive technical backgrounds can operate the software efficiently.
Performance Analysis
In terms of performance, Predator stands out as a high-performing tool that can handle large data volumes without significant slowdowns. It uses minimal system resources while maintaining robust threat detection capabilities. User reviews indicate that the software performs reliably even in complex network environments.
The efficiency of real-time analysis contributes significantly to its performance reputation. The ability to quickly identify and respond to threats lends itself to maintaining a secure network infrastructure without excessive downtime or operational friction.
Benefits of Using Predator
- Enhanced Security: By implementing Predator, organizations can significantly enhance their security measures, which is crucial in today’s threat landscape.
- Simplicity and Accessibility: Its user-friendly interface makes it accessible for both seasoned professionals and those new to cybersecurity practices.
- Cost-Effective Solution: Given its extensive feature set and effectiveness, many users find Predator to be a cost-effective solution for their cybersecurity needs compared to competitors.
- Regular Updates: The software regularly receives updates to address emerging threats and enhance functionality based on user feedback, ensuring it remains relevant in a rapidly evolving field.
Potential Drawbacks
- Learner Curve: Although the software is user-friendly, some users may initially struggle with understanding all features fully. Additional training sessions or tutorials may be beneficial.
- Pricing Variations: While Predator is generally viewed as cost-effective, the pricing model may deter smaller organizations with limited budgets compared to larger entities that find it justifiable.
User Feedback
User feedback for Predator has generally been positive. Professionals commend the software for its reliability and capacity to adapt to various organizational needs. Many point out the effectiveness of its real-time threat detection system as a crucial factor in their decision to use it over other products in the market.
This user satisfaction is bolstered by the responsive customer support team who assist users promptly regarding issues or queries related to the application.
Final Thoughts
Predator by Richard Goutorbe stands as a formidable option in the cybersecurity arena, promoting stronger network protection while ensuring ease of use through its intuitive interface. Its comprehensive features cater nicely to modern security demands and assist organizations in becoming more proactive in their approach to threat management. The software's ability to integrate seamlessly into existing systems adds to its appeal, making it suitable for a wide variety of industries seeking enhanced security measures.
As cybersecurity incidents continue to rise, incorporating such advanced tools like Predator could be pivotal in fortifying defenses against evolving threats. Organizations looking for a reliable partner in cybersecurity should consider further exploring this application as part of their security strategy.
Обзор
Predator — это Коммерческий программное обеспечение в категории Безопасность, разработанное Richard Goutorbe.
Пользователи нашего клиентского приложения UpdateStar проверяли Predator наличие обновлений 31 раз за последний месяц.
Последняя версия Predator-3.7.3.700 , выпущенный на 08.02.2017. Первоначально он был добавлен в нашу базу данных на 23.08.2016.
Predator работает на следующих операционных системах: Windows.
Predator не был оценен нашими пользователями еще.
Установки
Последние обзоры
|
|
EASEUS Partition Master Home Edition
EASEUS Partition Master Home Edition: Эффективное программное обеспечение для управления разделами |
|
|
PC Fresh
Оптимизируйте свой ПК для достижения максимальной производительности с помощью PC Fresh! |
|
|
Nero RescueAgent
Nero RescueAgent: Ваше решение для восстановления данных |
|
|
Software Informer
Будьте в курсе событий с помощью Software Informer |
|
|
NVIDIA RTX Desktop Manager
Оптимизируйте работу с настольным компьютером с помощью NVIDIA RTX Desktop Manager |
|
|
UzCrypto
Безопасный криптокошелек и приложение для управления портфелем |
|
|
UpdateStar Premium Edition
Обновлять программное обеспечение еще никогда не было так просто с UpdateStar Premium Edition! |
|
|
Microsoft Edge
Новый стандарт в просмотре веб-страниц |
|
|
Google Chrome
Быстрый и универсальный веб-браузер |
|
|
Microsoft Visual C++ 2015 Redistributable Package
Повысьте производительность системы с помощью распространяемого пакета Microsoft Visual C++ 2015! |
|
|
Microsoft Visual C++ 2010 Redistributable
Необходимый компонент для запуска приложений Visual C++ |
|
|
Microsoft OneDrive
Оптимизируйте управление файлами с помощью Microsoft OneDrive |